Have you ever wondered how your personal information stays safe when you are browsing the web or shopping online? It is all thanks to the SSL ports and HTTPS! These two work hand in hand to create a secure connection between your web browser and the websites you visit. In this blog, we will explore the world of SSL ports and HTTPS find their inner workings, and learn how they play in securing our digital activities.
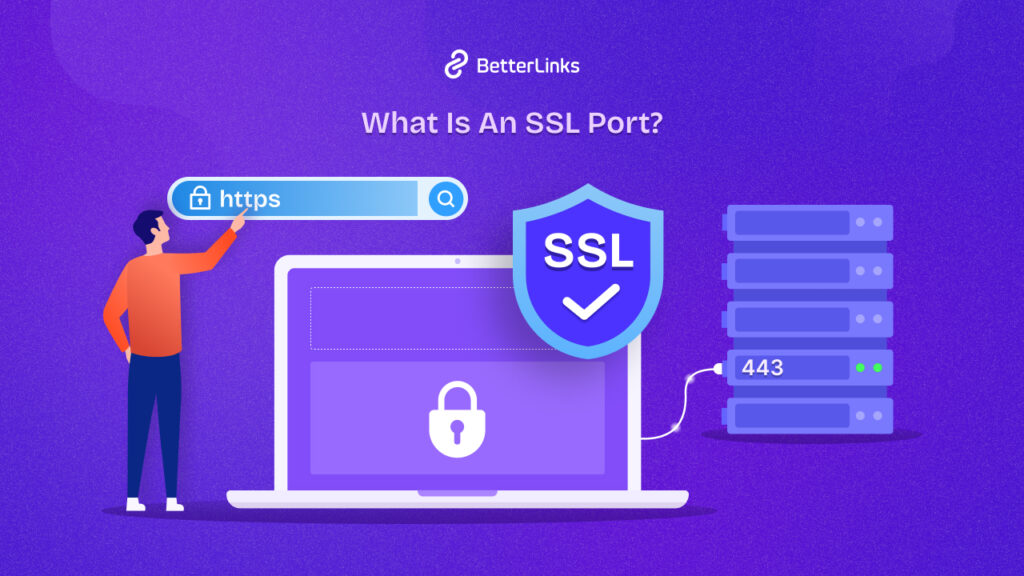
Importance of SSL Port in Securing Data
An SSL port is a type of TCP (Transmission Control Protocol) port that is used to establish secure communications over the Internet. SSL, which stands for Secure Sockets Layer, is a protocol used to encrypt data transmitted between a client (such as a web browser) and a server.
SSL port play a critical role in securing data by enabling encrypted connections. When data is transmitted over the internet without encryption, it can be intercepted and read by malicious actors. SSL ports ensure that the data is encrypted before transmission, making it unreadable to anyone who might intercept it.
This encryption process involves the use of SSL port certificates, which authenticate the identity of the server and establish a secure connection. By securing data in transit, SSL port protect sensitive information such as login credentials, personal details, and financial transactions. This is essential for maintaining privacy and security in online communications and transactions.
Common SSL Port And Layers
SSL (Secure Sockets Layer) and its successor, TLS (Transport Layer Security), utilize specific ports to establish secure connections for various protocols. Here are some of the most common SSL/TLS ports:

Port 443: Default Port for HTTPS Traffic
Port 443 is the default port used for HTTPS (HyperText Transfer Protocol Secure) traffic. HTTPS is the secure version of HTTP, the protocol used for transmitting web pages over the internet. When a web browser connects to a server using HTTPS, it uses port 443 to establish a secure connection. This port ensures that all data exchanged between the browser and the server is encrypted, providing a secure browsing experience.
Port 465: Used for Secure SMTP (Email) Communications
Port 465 was originally assigned for SMTPS (SMTP over SSL). However, it was deprecated in favor of STARTTLS on port 587. Some legacy systems still use port 465, but it’s not the modern standard for secure email communication.
Port 993: Used for Secure IMAP (Email) Communications
Port 993 is used for secure IMAP (Internet Message Access Protocol) communications. IMAP is a protocol used by email clients to retrieve messages from a mail server. By using port 993, email clients can securely access and manage their emails on the server. This port ensures that the email data is encrypted, protecting it from unauthorized access.
Port 8443: Often Used as an Alternative HTTPS Port
Port 8443 is often used as an alternative HTTPS port. While port 443 is the standard for HTTPS traffic, port 8443 can be used in situations where the default port is unavailable or needs to be avoided due to conflicts. This port is commonly used by web servers and network devices, such as Apache Tomcat, to provide secure web services. It offers the same level of encryption and security as port 443.
Understanding HTTPS
HTTPS (Hypertext Transfer Protocol Secure) is an extension of HTTP, the protocol used for communication over the web. HTTPS adds a layer of security to HTTP by using SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols to encrypt data between the browser and the web server.

How HTTPS Secures Communication
HTTPS secures communication through the use of SSL/TLS protocols, which encrypt data transmitted between a user’s browser and the web server. Here is a step-by-step explanation of how this process works:
- Browser Contacts Website: When a user attempts to connect to a website using HTTPS, their browser sends a request to the web server.
- SSL/TLS Certificate Exchange: The server responds by sending its SSL/TLS certificate, which includes the server’s public key.
- Certificate Verification: The browser verifies the certificate to ensure it is valid and issued by a trusted Certificate Authority (CA).
- Encryption Key Exchange: Once the certificate is verified, the browser and server use the public key to exchange a symmetric session key securely.
- Secure Data Transfer: All subsequent data transferred between the browser and the server is encrypted using this session key, ensuring that it cannot be read by anyone intercepting the data.
Key Differences Between HTTP and HTTPS
The primary advantage of HTTPS over HTTP is the enhanced security it provides. HTTPS ensures that data transmitted between the browser and server is encrypted, authenticated, and protected from tampering:
- Security: The primary difference between HTTP and HTTPS lies in the level of security they provide. HTTP transmits data in plaintext, making it vulnerable to eavesdropping and tampering. HTTPS, on the other hand, encrypts the data using SSL/TLS, ensuring that the information remains confidential and intact during transmission.
- Port: HTTP uses port 80 for communication, while HTTPS uses port 443.
- URL Prefix: Websites using HTTP have URLs that begin with “http://“, whereas websites using HTTPS have URLs starting with “https://“.
- SSL Certificates: HTTPS requires websites to obtain and install SSL certificates from trusted authorities. These certificates verify the website’s identity and enable secure encrypted connections.
- Performance: Due to the additional encryption and verification processes, HTTPS connections may be slightly slower than HTTP connections. However, the performance difference is minimal and often negligible, especially with modern web technologies and hardware
Role of SSL/TLS Protocols in HTTPS
SSL (Secure Sockets Layer) and its successor TLS (Transport Layer Security) are cryptographic protocols that provide secure communication over a computer network. Here is how SSL/TLS works to establish secure connections:
- Intro Process: When a browser connects to a server using HTTPS, the SSL/TLS Intro process begins. This involves the exchange of cryptographic keys to establish a secure session.
- Certificate Authentication: The server presents its SSL/TLS certificate to the browser. The browser verifies the certificate against a trusted CA to ensure the server’s identity.
- Key Exchange: The browser and server use asymmetric encryption (public and private keys) to securely exchange a symmetric session key.
- Symmetric Encryption: Once the session key is established, it is used for symmetric encryption of data. Symmetric encryption provides a faster and more efficient solution for continuous data transmission.
- Data Integrity: SSL/TLS ensures data integrity by using message authentication codes (MACs) to detect any tampering during transmission.
SSL Ports Are Used to Initiate and Maintain HTTPS Connections
SSL (Secure Sockets Layer) ports play a crucial role in establishing and maintaining secure HTTPS (Hypertext Transfer Protocol Secure) connections. When a user attempts to access a secure website, the following process typically occurs:
- Connection Request: The user’s web browser sends a request to the server using HTTPS, which defaults to port 443. This port is specifically designated for secure web traffic.
- SSL/TLS Handshake: The browser and server initiate an SSL/TLS handshake. During this handshake, they agreed on the encryption methods to be used to exchange cryptographic keys. This step ensures that both parties can securely communicate.
- Session Key Generation: Both the browser and server generate session keys for symmetric encryption. These keys are used to encrypt and decrypt the data exchanged during the session.
- Secure Data Transfer: Once the handshake is complete, an encrypted tunnel is established over port 443. All subsequent data transferred between the browser and server is encrypted, ensuring confidentiality and integrity.
Significance of Using the Correct SSL Port
SSL ports play a crucial role in securing our online communications, with port 443 being the star of the show for HTTPS traffic. When you visit a website and see that little padlock icon in your browser’s address bar, you can thank port 443 for making that secure connection possible. This port is like a special gateway that allows encrypted data to flow between your device and the web server, keeping your sensitive information safe from prying eyes.
But why is port 443 so important? Well, it is the standard port for HTTPS, which means it is universally recognized and supported by web browsers and servers worldwide. This standardization ensures that secure connections can be established seamlessly, no matter where you are or what device you are using. Plus, for businesses handling online transactions, using HTTPS over port 443 is not just a good practice—it is often a requirement for compliance with security standards like PCI DSS.
While port 443 gets most of the attention, other SSL ports exist for specific purposes. For example, port 993 is used for secure IMAP email connections, and port 995 is for POP3S. These ports work similarly to 443, providing encrypted channels for different types of internet traffic.
Potential Issues with Using Non-Standard Ports
SL ports are crucial in establishing secure HTTPS connections between web browsers and servers. While port 443 is the standard SSL port for HTTPS traffic, other ports like 465 for SMTP and 993 for IMAP are also commonly used for secure communications. Although it is possible to configure web servers to use non-standard SSL ports, this practice is generally not recommended for public-facing websites.
Using non-standard ports can lead to compatibility issues, reduced security, and negative impacts on SEO and performance. Sticking with the widely recognized and supported port 443 for HTTPS traffic is the best approach for most websites. This ensures maximum compatibility, security, and visibility for your website. Remember, the goal of SSL is to provide secure, encrypted connections, and using standard ports helps achieve this goal while maintaining broad accessibility for users across the internet.
We hope you found this blog helpful and if you want to read more exciting blogs, stay to up to date with the latest Shopify news – subscribe to our blog page and stay tuned!